 Duration - 3 Month, 8-10 hours/week
Duration - 3 Month, 8-10 hours/week
 Course fee: - INR 35000
Course fee: - INR 35000
What is the CIPM qualification?
The CIPM designation manifests that you’re a leader in privacy program administration and that you've got the knowledge to establish, maintain and manage a privacy program across all stages of its life cycle.
WHY CIPM?
- The CIPM is the global industry standard in privacy programme management.
- Master the skills to establish, maintain and manage a privacy programme across all stages of its operational lifecycle.
- Bear the mark of a privacy leader who drives the culture of privacy within your organisation.
- Elevate your leadership profile among your colleagues.
- Secure the confidence that you have the essential tools and knowledge to boost your privacy programme and add value across your organisation in both the public and private sectors.
What kind of positions/roles can you get if you possess the CIPM qualification?
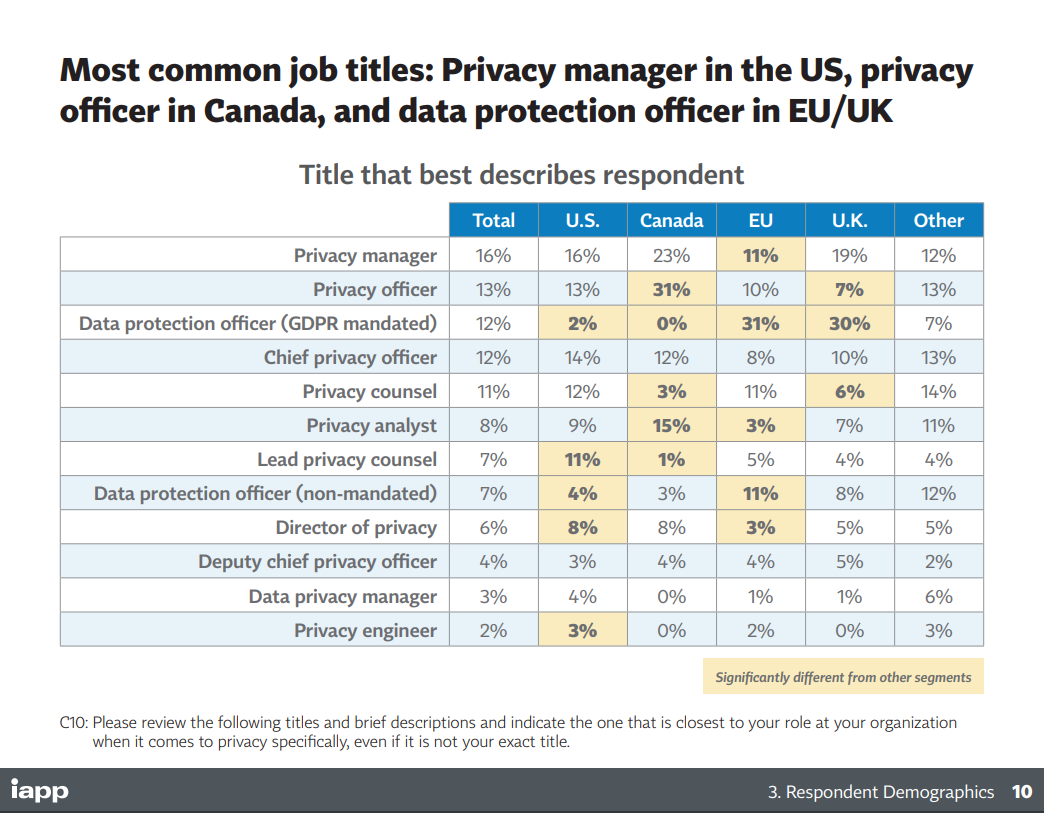
What kind of organisations need to hire people who have a CIPM qualification?
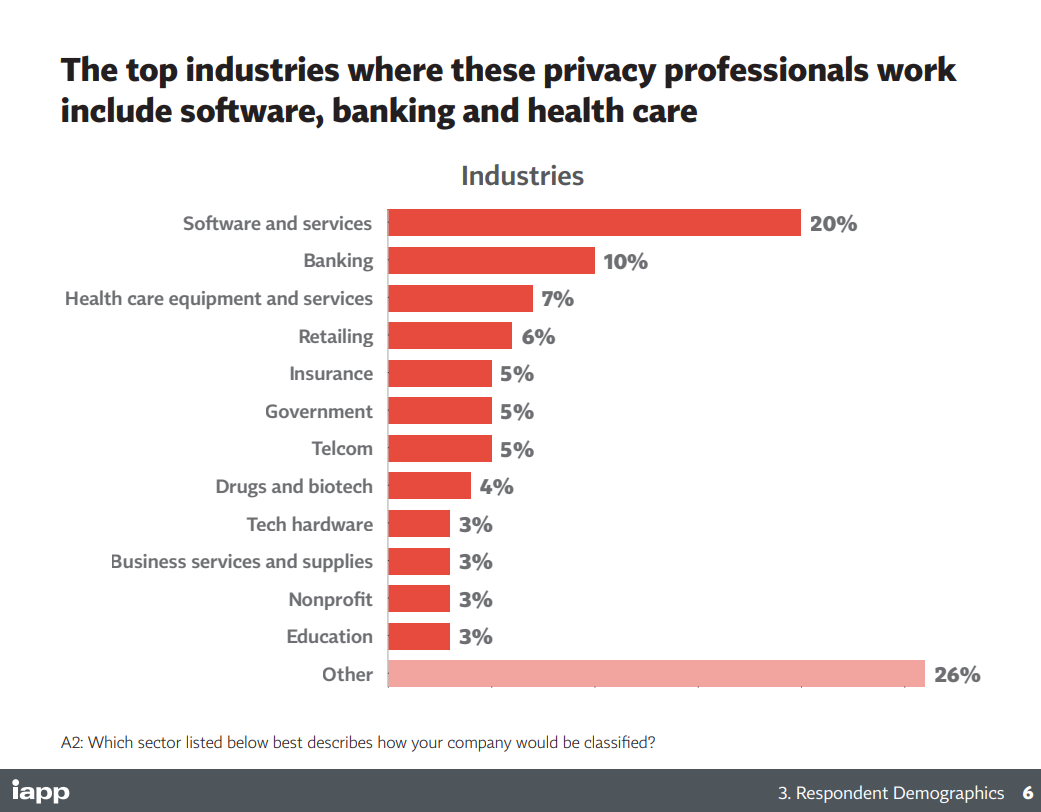
What is the work that you have to do as a privacy manager?
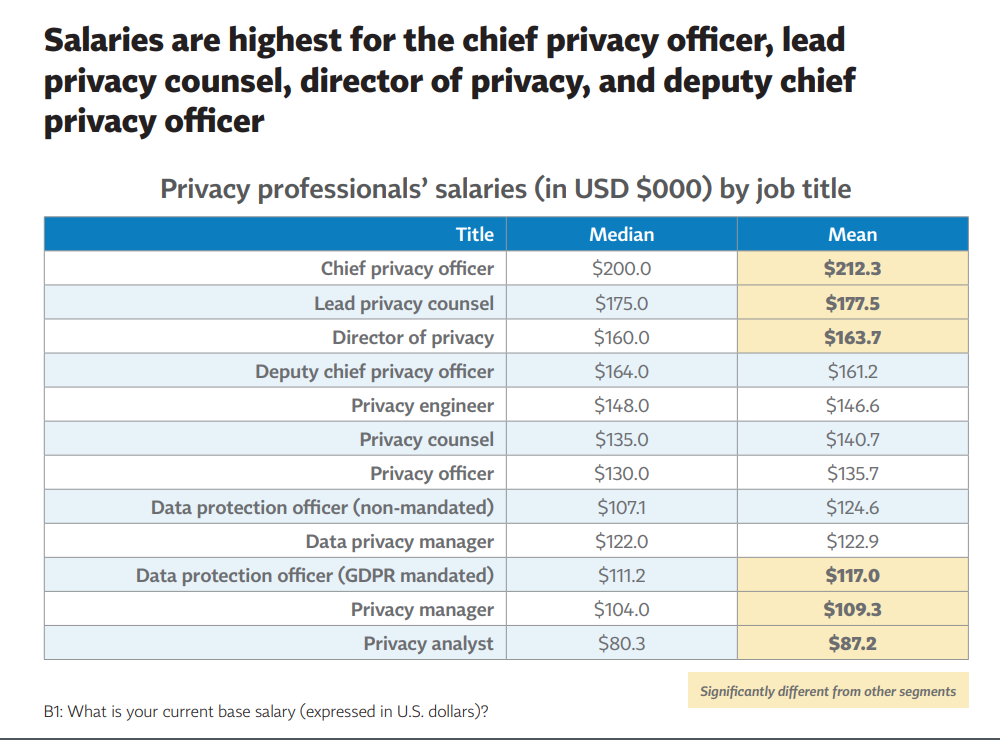
Who is eligible to crack the CIPM Exam?
No specific eligibility requirements. Undergrad students can attempt the exam.
About the Exam
All IAPP exams are difficult to pass without adequate preparation. For the CIPM exam, you will get 90 multiple-choice questions. Each of the 90 questions will have four options in which you will be required to choose the correct answer. Most times, the four options are quite similar, and you will need an in-depth understanding of the topics to pick the right answer.
You have 2.5 hours to complete the exam and must score above 300 points to pass the test; that’s about 65% – 80%. We know each question carries equal value, but how the points are awarded isn’t known to the public yet.
How is CIPM different from CIPP?
CIPP is about the substantive privacy rules in the US/EU/Canada. In CIPM, the emphasis is on managing privacy. And less on knowledge of the substantive rules.
CIPM is about shaping Privacy program management. Questions that arise are why is a privacy program necessary? How do you manage that?
This involves creating an organizational privacy vision and mission statement, how to select the right Privacy Framework, develop a Privacy Strategy and structure a Privacy Team.
Can I do CIPM without having done CIPP?
Yes, there is no requirement to do CIPP before CIPM.
If I have CIPP should I also consider doing CIPM? What could the additional benefit be?
The CIPP certification helps in gaining the substantial knowledge of laws and regulations that govern the Privacy arena in a particular jurisdiction, however, CIPM is not about laws and regulations, it is more about implementation of privacy program, strategy, team structure and team management.
Which organisations need to establish a privacy program? What are the components of a privacy program?
Every company that is subject to privacy laws, whether GDPR, CCPA, PIPEDA or LGPD, must establish a privacy program.
Some of the components of a privacy program include a business plan for privacy implementation, structuring a privacy team with internal and external stakeholders, identification of which categories of data need protection, review of information privacy standards and regulations, audit frameworks, and deployment of an employee awareness and training program.
Money-back guarantee
If you take this course, follow it diligently for a month, do all the exercises but still do not find value in it, or not able to understand or follow it or not find it good for any reason, we will refund the entire course fee to you. It is a 100% money-back guarantee with only one condition, you must pursue it properly for a month. If you don’t find it valuable after that, get your entire money back.
Training Methodology

Online 24/7 access
Access to basic study material through an online learning management system, Android and iOS app

Hard Copy Study Material
Hard copy study material modules to be couriered to your address

Live Online Classes
Based on the exercises, there will be a live video-based online class. You can ask questions, share your screen, get personal feedback in this class.

Convenient Class timings
Classes are held after regular work hours. Typically classes are kept on Sunday afternoon or 8-9 pm on other days.

Live Doubt Clearing
You can ask questions, get your doubt cleared live as well as through online forums
Syllabus
Developing a Privacy Program for example policies 
![]() Create an organizational vision
Create an organizational vision
![]() Establish a Data Governance model
Establish a Data Governance model
![]() Define a privacy program
Define a privacy program
![]() Structure the privacy team
Structure the privacy team
![]() Communicate with Stakeholders internally and externally
Communicate with Stakeholders internally and externally
Privacy Program Framework for example stakeholder discussions 
![]() Develop and implement the Privacy Program Framework
Develop and implement the Privacy Program Framework
![]() Develop organizational privacy policies, procedures, standards, and/or guidelines
Develop organizational privacy policies, procedures, standards, and/or guidelines
![]() Define privacy program activities
Define privacy program activities
i. Education and awareness
ii. Monitoring and responding to the regulatory environment
iii. Monitoring internal privacy policy compliance
iv. Data inventories, data flows, and classifications designed to identify what personal data your organization processes
v. Risk assessment (Privacy Impact Assessments [PIAs]) (e,g., DPIAs etc.)
vi. Incident response and process, including jurisdictional requirements
vii. Remediation oversight
viii. Program assurance, including audits
ix. Plan inquiry/complaint handling procedures (customers, regulators, etc.)
Develop Appropriate Metrics 
![]() Identify intended audience for metrics
Identify intended audience for metrics
![]() Define reporting resources
Define reporting resources
![]() Define privacy metrics for oversight and governance per audience for example
Define privacy metrics for oversight and governance per audience for example
Compliance metrics (examples, will vary by organization) that includes Collection (notice), Responses to data subject inquiries, Retention, Disclosure to third parties, Incidents (breaches, complaints, inquiries), Employees trained, PIA/DPIA metrics, Privacy risk indicators, Percent of company functions represented by governance mechanisms, Trend Analysis, Privacy program return on investment (ROI), Business resiliency metrics, Privacy program maturity level and Resource utilisation.
![]() Identify systems/application collection points
Identify systems/application collection points
Privacy Operational Life Cycle: Assess for example awareness trainings 
![]() Document current baseline of your privacy program
Document current baseline of your privacy program
a. Education and awareness
b. Monitoring and responding to the regulatory environment
c. Assess policy compliance against internal and external requirements
d. Data, systems and process assessment
i. Map data inventories, flows, lifecycle and system integrations
e. Risk assessment methods
f. Incident management, response and remediation
![]() Processors and third-party vendor assessment
Processors and third-party vendor assessment
a. Evaluate processors and third-party vendors, insourcing and outsourcing privacy risks, including rules of international data transfer
i. Privacy and information security policies
ii. Access controls
iii. Where personal information is being held
iv. Review and set limits on vendor internal use of personal information
b. Understand and leverage the different types of relationships
i. Internal audit
ii. Information security
iii. Physical security
iv. Data protection authority
c. Risk assessment
i. Type of data being outsourced
ii. Location of data
iii. Technologies and processing methods deployed (eg Cloud Computing)
iv. Legal compliance
v. Records retention
vi. Contractual requirements (incident response, etc.)
vii. Determine minimum standards for safeguarding information
viii. Cross-border transfers
d. Contractual requirements and review process
e. Ongoing monitoring and auditing
![]() Physical assessments
Physical assessments
a. Identify operational risk
i. Data centers and offices
ii. Physical access controls
iii. Document retention and destruction
iv. Media sanitization and disposal (e.g., hard drives, USB/thumb drives, etc.)
v. Device forensics
vi. Device security (e.g., mobile devices, Internet of Things (IoT), geotracking, imaging/copier hard drive security controls)
![]() Mergers, acquisitions and divestitures
Mergers, acquisitions and divestitures
a. Due diligence procedures
b. Review contractual and data sharing obligations
c. Risk assessment
d. Risk and control alignment
e. Post integration planning and risk mitigation
Privacy Operational Life Cycle: Protect for example ensuring technical measures 
![]() Technical and Organizational measures
Technical and Organizational measures
Privacy Operational Life Cycle: Sustain for example compliance audits 
![]() Monitor
Monitor
a. Environment (e.g., systems, applications) monitoring
b. Monitor compliance with established privacy policies
c. Monitor regulatory and legislative changes
d. Compliance monitoring (e.g. collection, use and retention)
i. Internal audit
ii. Self-regulation
iii. Retention strategy
iv. Exit strategy
![]() Audit
Audit
a. Align privacy operations to an internal and external compliance audit program
i. Knowledge of audit processes and maintenance of an “audit trail”
Privacy Operational Life Cycle: Respond for example Data Breach Mgmt 
![]() Data-subject information requests and privacy rights
Data-subject information requests and privacy rights
![]() Privacy incident response
Privacy incident response
![]() Incident detection
Incident detection
![]() Incident handling
Incident handling
![]() Follow incident response process to ensure meeting jurisdictional, global and business requirements
Follow incident response process to ensure meeting jurisdictional, global and business requirements
![]() Identify incident reduction techniques g. Incident metrics—quantify the cost of a privacy incident
Identify incident reduction techniques g. Incident metrics—quantify the cost of a privacy incident
Course Plan
Standard
₹ 35000
incl. of all charges
-Printed study material (by courier)
-1 online live class/ week
-2 practical or drafting exercises per week
-Get digital access to entire study material
-Access on LMS, Android & iOS app
-Instructor feedback on assignments
-Unlimited doubt clearing sessions.
-Instructor led course with online live classes
-Online exams (give exams as per your convenience on given time slots)
-Certificate (by courier)
-CV enhancement
-Coaching for professional networking
-Training for writing and publishing articles
-Internship & Job Support
-Interview preparation guidance
-Access to updated content online for 3 years
-Top students are recommended to law firms and companies (as applicable)


 US
US
 IN
IN
 UK
UK





 featured
featured